Navigation: Security Screens >
Use the Security > Reports screen to view and print reports for security setup and changes made to most GOLDPoint Systems programs.* This is especially helpful if you want to view what security changes have occurred, or you want to see if security changes were made for a specific employee.
|
Note: Security changes made to GOLDTrak® PC security are not included. GOLDTrak® PC security is set up in GOLDTrak® PC Setup. |
|---|
For information and definitions for security systems, see System Security Definitions.
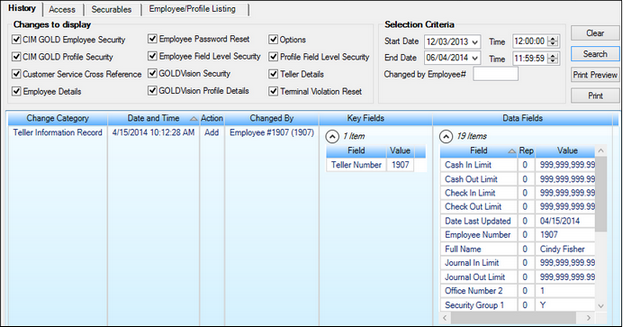
Security > Reports Screen
Tabs
Selection criteria are specific for each tab, based on the function of the screen. See the linked help for each tab for more information.
•The History tab is used to report and print changes made to CIM GOLD security using CIM GOLD. You can limit searches to profiles, to employee and teller details, or to other criteria.
•The Access tab allows you to select any employees, profiles, or tellers and display or print the access that has been granted in CIM GOLD security. You can also refine your search to include only some or all of the access for employee details, CIM GOLD, System, teller details, and field-level security. If multiple profiles are assigned, the "effective" security will be determined.
•The Securables tab allows you to select any applications, Systems, or screens and display or print the employees and profiles that have been granted security for them in CIM GOLD Security. The report can also display employees and CIM GOLD profiles that are restricted by field-level security. If multiple profiles are assigned, the "effective" security will be determined.
•The Employee/Profile Listing tab allows you to include employees and profiles and to generate and print a detail report of employee/profile setup information (Employee Numbers, Employee or Profile Type, Status, User Name, Timeout, and Password Expiration). The report will also show which employees are sharing CIM GOLD or System profiles. You can sort the information by Full Name, System Profile, Employee/Profile Number, Password Expiration, Status, Timeout, Employee/Profile Type, and User/Profile Name. Security for employees and profiles are set up on the Security > Setup screen.
|
Tip: One common security option involves allowing users to view or maintain employee accounts. You set this option on the System tab of the Setup screen. Under PC Applications, set any of the following fields to None, Inquire, or Maintain:
CIM Can See Employee Dep Hist (bit 38) CIM Can See Employee Ln Accts (bit 37) CIM Can See Employee Ln Hist (bit 32) CIM Can View Employee Accts (bit 26)
To search for incidences when the employee account options were changed, access the Reports screen and complete the following steps:
In the example below, you can see that employee number 1907 had security bit #26, 32, 37, and 38 changed from INQ (inquiry) to F/M (maintain). See System Security for a definition of all system security codes.
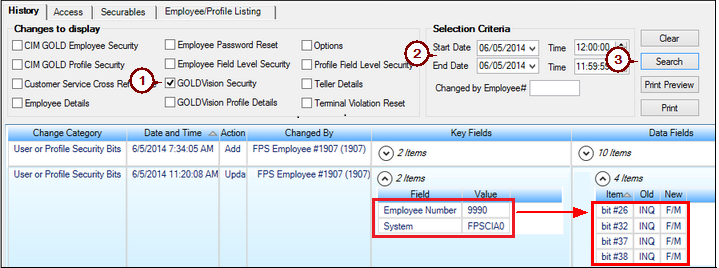 |
|---|
In order to use this screen, your institution must:
•Subscribe to it on the Security > Subscribe To Mini-Applications screen.
•Set up employees and/or profiles with either Inquire (read-only) or Maintain (edit) security for it on the CIM GOLD tab of the Security > Setup screen. |
See also: