Navigation: »No topics above this level«
The Security system in CIM GOLD contains all information and functions relating to security options at your institution.
For ease of use, this online help is designed to match the layout of Security screens in the CIM GOLD tree view, as shown below:
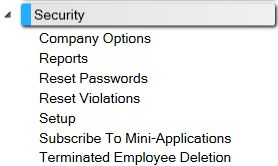
Before you can use CIM GOLD or other GOLDPoint Systems applications, security must be set up for each employee. Only your institution's security administrator will have access to these screens.
See any of the following topics for more information concerning the screens under Security:
•Subscribe to Mini-Applications
Security Setup Order
The following list shows the order in which security must be set up within CIM GOLD so that security will work properly for your institution and employees.
NOTE
GOLDPoint Systems must add security for your institution’s Security Administrator before employee security setups can begin. Additionally, GOLDPoint Systems' Network Control Center must assign a user name and password for each employee upon initially logging on to any GOLDPoint Systems program. Contact your client solutions specialist for more information: (888) 477-0099. |
| 1. | Subscribe to Mini-Applications - Before security setup, your institution must subscribe to all applications and screens your institution will use. |
| 2. | Company Options - The fields on this screen define your institution name, length of employee numbers and passwords, days to force security code (password) changes, and minutes of inactivity to timeout CIM GOLD and other GOLDPoint Systems products. Company Options are found on the CIM GOLD Security > Company Options screen. |
| 3. | Setup - Contains setup fields for employee, profile, teller security, CIM GOLD screens, and field-level security. If your institution chooses to use profiles, they must be set up before setting up individual employees. |
| 4. | If you want to run reports to see who has access to which screens, as well as what security options were changed, use the Reports screen. |