Navigation: Security Screens >
The Reset Violations screen is located in CIM GOLD under Security > Reset Violations. This screen is used to reset a password after the user has entered an incorrect password three consecutive times while attempting to log in. A user cannot sign on to CIM GOLD until the violation has been cleared using this screen. GOLDPoint Systems recommends that only a limited number of employees be given security to reset violated terminals.
|
Note: GOLDPoint Systems cannot reset security violations for your employees. An employee at your institution must handle this function. |
|---|
If there are security violations active at your institution, they will appear in the list view on this screen.
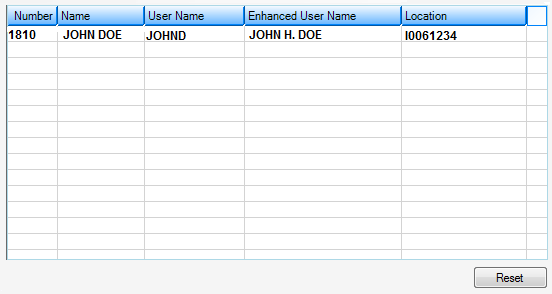
Security > Reset Violations Screen
To clear a violation, highlight the name in the list and click the ![]() button on the bottom of the screen. The reset will clear the violation, and the user can attempt to log on again with their current password.
button on the bottom of the screen. The reset will clear the violation, and the user can attempt to log on again with their current password.
|
Note: Resetting violations does not change the password to the user name. A password is only reset to the user name by resetting the password on the Security > Reset Passwords screen. This function would instead be used if a user forgets his or her password. |
|---|
See the following paragraphs for quick descriptions of each of the columns in the Reset Violations list view.
Column |
Description |
|---|---|
Number |
This column displays the employee number for the user who caused the violation. |
Name |
This column displays the name of the employee with the security violation. |
User Name |
This field displays the user name of the user who caused the violation. This field is used on CIM GOLD screens and afterhours reports. |
Enhanced User Name |
This field displays the long user name (if your institution has entered this data) for the employee with the violation. |
Location |
This field displays the PC VTAM location of where the security violation occurred. The VTAM can be thought of as the actual computer's identity within the security system. |
In order to use this screen, your institution must:
•Subscribe to it on the Security > Subscribe To Mini-Applications screen.
•Set up employees and/or profiles with either Inquire (read-only) or Maintain (edit) security for it on the CIM GOLD tab of the Security > Setup screen. |
See also: