Navigation: Security Screens > Setup Screen >
Use the fields on the System tab of the Security > Setup screen to set up security for other systems, as well as specific functions within CIM GOLD. See System Security Details for detailed information concerning each of the settings on this tab.
Using this tab you can set up security for the Accounting system, GOLDTeller, GOLDView, Web security, and much more.
|
Note: GOLDTrak security is not set up using this tab. GOLDTrak security has its own security program in the GOLDTrak PC Setup application. |
|---|
|
Tip: Before making any changes to security, the Display Effective Security box on the Security > Setup screen must be unchecked. |
|
Tip: Changes to security requires users to close down the application they are using and log onto it again before changes take affect. For that reason, we suggest you not update or change security until a time when no users are on the system. |
|
WARNING: Some users may be tied to a profile, or even two profiles, as well as have their own personal security settings. The system allows the highest security options available to that employee based on their profile or user security settings. The ranking of security settings are:
•Highest - Maintain •Middle - Inquire •Lowest - None
For example, employee Sally is tied to two profiles, Teller and Accounting, as well as her own security settings.
•The Teller Profile restricts Sally from accessing the Customer Relationship Management > Households screen (security setting for that screen is set to None).
•The Accounting Profile allows inquiry-only access to the Customer Relationship Management > Households screen (security setting for that screen is set to Inquire).
•Sally's personal security is set so that she has file maintainable access to the Customer Relationship Management > Households screen (security setting for that screen is set to Maintain).
In this example, Sally would be able to access the Households screen and view, create, and make changes to households based on her personal security settings, even though the two profiles she's connected to would either not allow access or allow inquiry-only access.
See the CIM GOLD Profile tab in the Security in CIM GOLD manual on DocsOnWeb for more information on how to set up System Profiles.
Field-level security does not affect fields in WinTerm/GOLDVision; it is only for CIM GOLD. |
|---|
This tab is used to set up security for employees or profiles (selected in the Security Setup list view) that need to have access to functions in other GOLDPoint Systems programs. This tab will be disabled if you have not selected either the Employees or System Profiles radio buttons. Use the Search field to quickly locate a particular security option on this field (all security options containing the letters typed will be highlighted in yellow).
Some of the applications listed on the System tab are obsolete. Please be aware that many security options to other programs are found under PC Applications, such as access to CIM GOLD, access to EFT GOLD, ability to view and change employee accounts, etc. See the following example of the security options under PC Applications:
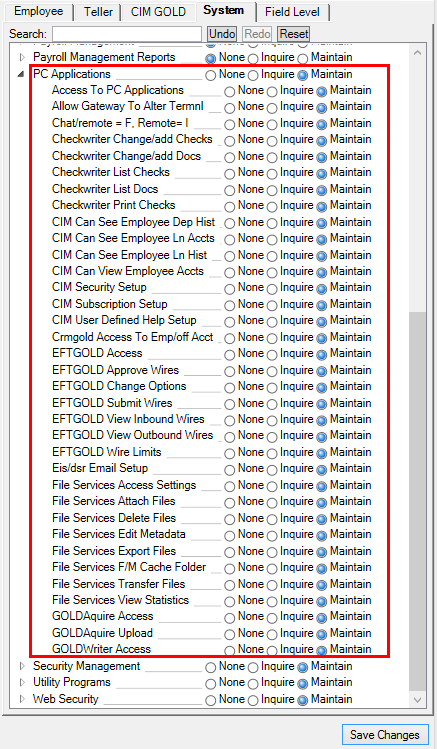
|
Tip: The security settings on the System tab on the Security > Setup screen in CIM GOLD are the exact same settings as those found in Application 19, Security Maintenance, in GOLDVision/WinTerm, as shown below. Any changes you make to those security settings will also affect the security settings on this tab in CIM GOLD, and vice versa.
|
Each system listed on this tab has a code. This is best explained with an example from the System tab, as shown below. The Accounts Receivable code is AR01000, the Additional Loan Security code is FPSSEC1, etc.
Knowing each code is helpful when viewing reports on the History tab of the Security > Reports screen, as search results show the code but not the system name. In the example below, you can see that seven security options for code FPSCFMN (Customer Information File) were changed for employee number 1907.
Bit is a programming term used to mean the radio button you select to turn on or off an option. If you hover your mouse over a radio button on the System tab of the Security > Setup screen, a tool-tip pop-up is displayed that identifies what the bit is, as shown below.
Therefore, in the Data Fields column on the Reports screen, you can see exactly which bit was changed.
The following table explains each of the system codes. For a definition of each of the bits, see the tooltip pop-up on the System tab.
|
For a list of all possible system security options and their bit numbers, see the System Security Details page.
 |
GOLDPoint Systems Only: If you are assisting a client with System security and logging into CIM GOLD as an editor, you will need to make sure your Terminal Table Configuration is set up correctly. Otherwise, you will not be able to see any settings on the System tab. Make sure you have "FPS" in the Initial Program field, instead of "GPS" (see below):
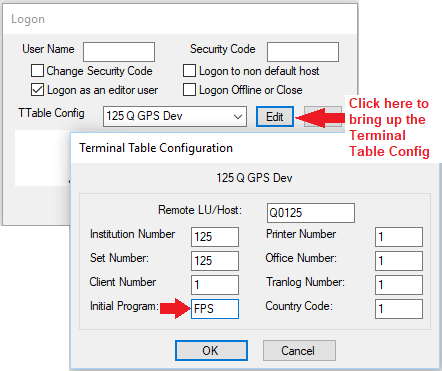 |
|---|